Protect Yourself from Cybercrime: Top 5 Smart Strategies In 2024
Cyber crimes are increasing day by day as the use of the internet is penetrating globally. These crimes are not just limited to hackers stealing your financial and personal information. Cyber threats are far more dangerous than we usually hear on the news.
These attacks usually target to disrupt, destroy, and steal the data of your computer system. It is the need of the hour to learn cybersecurity practices so that you can avoid these threats and protect your data.
Cybersecurity measures are very necessary for edtech platforms and organizations which provide free term papers on literature and PhD dissertation writing services because they have vital academic data.
There are a variety of practices and measures you can use to save yourself. In this write-up, we will learn the 5 best strategies to protect yourself from cybercrime.
What Is Cybercrime?
Cybercrimes are the crimes that take place in the internet world. There are different types of cyber crimes like Malware attacks, Phishing, Distributed DoS attacks, etc.
Malware attacks affect computer systems with viruses and corrupt the data. It steals the confidential data of the victim and carries out criminal activities.
For instance, one of the most popular cybercrimes in recent years was the WannaCry ransomware attack. This was committed in May 2017 and used loopholes in the Windows system to extort money from the systems.
In phishing, a vulnerable link to sent to people with emails and messages. When someone clicks on that link, they get hacked and lose control of the system.
Top 5 Smart Strategies For Protection Against Cybercrimes In 2024
Government and private cybersecurity bodies are constantly making efforts to build a safe and secure online world. Although these threats can not be eliminated, we can try some effective measures.
There are some basic precautions everybody can use to protect themselves from phishing and cyber-attacks. Here are the top 5 smart ways to cop up cyber crimes.
Conduct Cybersecurity Risk Assessment
The first step of cybercrime prevention is to conduct a thorough cybersecurity risk assessment so that you can find the potential vulnerabilities inside your system. This assessment provides you insights about what aspects you have to protect more.
Conducting a cybersecurity risk assessment can also help you set up an IT security team that can find the potential areas that can be exploited by hackers. You can also have a security rating for your organization.
Security ratings work as a quantifiable measure of your organization’s security posture. This process will help you highlight the weaknesses of your organization’s IT infrastructure that need immediate attention.
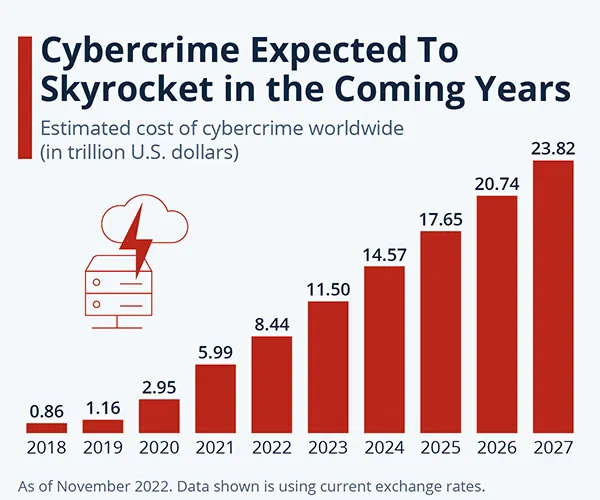
Interesting Fact:
The above graph shows the report of Statista on the increased number of cyber threats. The cost of cyber crimes is expected to reach $23.82 trillion by 2027.
Establish network access controls
When you have completed your assessment of cybersecurity risks, the next step is to establish network access control. It helps you identify the inside threats to your system. Nowadays, organizations are turning towards security system software to measure insider threats according to their functions.
Network access controls help organizations avoid the threats that occur due to employee negligence and lack of awareness. Consideration of endpoint security is also necessary when the number of connected devices increases.
The key strategy to cope with cyber crimes is to implement strict network access controls. Regular monitoring and updating of network access prevent unauthorized access and reduce the risk of cyber threats.
Regularly Update and Patch Systems:
Regular monitoring and updating of firewall and antivirus software is necessary to protect your system against the upcoming threats. Firewalls must be customized according to the needs of the organization and decide which traffic is potentially risky and which is safe.
On the other hand, regular monitoring of antiviruses is needed to find the latest risks and eliminate them. Software providers constantly release patches, but hackers are aware of that. Organizations must remember the patching schedule of their software provider to maintain an effective patch management schedule.
The patching process not only tracks and applies the solution but also verifies the vulnerabilities caused by this process. To maintain a robust cybersecurity system, you need to have a proactive approach regarding patch management.
Implement Strict Network Security Protocols:
Network security protocol helps to make secure internet surfing. These protocols are made up of strings of operations and ensure data safety. Organizations should use VPNs for extra protection and make the software installation strict. Internet security protocols are broadly classified into these 4 parts:
- Access Control: This protocol ensures that the right user gets access to the right resources. It verifies the identity of the user and decides to allow or deny their access.
- Algorithm Encryption: Encryption algorithms help organizations protect their unencrypted data and turn the plain text into ciphertext to tackle scammers and hackers.
- Key Management: It handles the encryption of keys and help to maintain, distribute, and create stronger passwords.
- Message Integrity: This protocol ensures that no one can read or hear the messages sent between two people and guarantees end-to-end encryption.
DO YOU KNOW?
95% of data breaches occur because of human errors. After COVID-19, when the number of work-from-home employees increased, the FBI reported an increase of 300% in cybercrimes.
Utilize Security Solutions:
Hackers and cyber criminals constantly develop new malware and phishing attacks to hack your system. If you take cybersecurity lightly, it can cause data breaches, financial loss, and reputational damage. Cybersecurity software products play a vital role in this condition.
These antivirus software scan files, emails, and web pages and find out the malicious activities. A variety of antivirus software is available in the market, both paid and free. The popular names among antivirus solutions are Norton, McAfee, Avast, Kaspersky, etc.
This software uses different methods and processes to prevent viruses. Free versions of antivirus are usually limited by features, that’s why it is recommended to spend some dollars and purchase a premium plan for better security.
Wrap Up
Cyber crimes can occur because of a variety of reasons including employee negligence, lack of awareness, or attacks from outside. The threat of cyber crimes is also increased with the penetration of the internet.
That’s why organizations must implement effective strategies to find out potential risks and eliminate them. In this article, we discussed the 5 effective measures to cope with these crimes.
Every individual and organization is advised to apply security protections on their data based on their resources. If you find this post helpful, share it with your friends working in IT and cybersecurity.
What Is Mobile Proxy And How Do They…
What Is Residential Proxy? Definition And Guide 2024
Strategies for Cyber Success: Safeguarding and Managing Your…
Cybersecurity Course Online: Navigating the Digital Threat Terrain
Are You Being Spied On? 5 Reasons Why…
Fortifying Your Online Fortress: Unveiling the Best Paid…
The Imperative of Cybersecurity Integration in Front-End Development…
10 Tricks for Staying Cyber-Secure While Binge-Watching
Securing Your System: The Importance of Anti-Malware Software
Benefits of VPN for Enterprise Networks: Enhanced Security
PureVPN – The Best Streaming VPN
L2TP vs. PPTP: Which VPN Protocol is More…