Are You Being Spied On? 5 Reasons Why You Should Protect Your IP Address
In an age when technology is progressing at lightning speed, there are increased cases of data theft by invading an IP address. Privacy is of concern for everyone, especially when most of our personal and business activities happen online.
From transactions to search history, audio, and video files, there is a lot that could be compromised if left unchecked. With an IP, anyone can detect all this information and misuse it causing huge losses.
Safeguarding the wealth of information needs strong security measures like robust software password protection and more. In this article, we provide all the reasons why and how anyone can take proactive action to protect their IP address.
Why Would Hackers Want Your IP?
Internet Protocol address is a series of numbers assigned to a network and all devices connected to it. It is relevant for exchanging data on the internet.
When a phisher uncovers an IP, they can use an IP tracker to learn more about their next target.
An Internet Protocol tracker can reveal someone’s country of residence, city, zip code, ISP, and even a time zone.
Collecting this information is just the first step in a cyberattack that could be launched for various reasons, some of which are listed below.
DO YOU KNOW?
Blue Hat Hackers (Blue Teams) are ethical hackers who are trained in cybersecurity and are invited by organizations to test their systems for vulnerabilities before a product launch or major update.
Reasons Why You Should Protect Your IP Address
While IP information alone is not of much use to phishers, various hacking methods and tools like trackers could give away more data and endanger privacy.
Here’s why protecting an Internet Protocol is fundamental:
Protecting your physical location
Once they obtain an internet address, hackers could expose a physical location. While they can’t tell you the exact place, Internet Protocol information will show them the neighborhood you live in, which is still quite alarming.
If they do a little bit of digging online and check social media profiles, cybercriminals will find out about the physical location.
It might not sound like a serious concern for some, but the reality is entirely different. When cyber thieves learn about a location, they are one step closer to identity theft.
They might use personal information to impersonate you online or even get their hands on finances. Not to forget that might lead to a stalker who has harmful intentions.
Keeping your devices free of malware
An Internet Protocol tracker can reveal more than just an estimated location. Cybercriminals could use it to get information about the gadgets owned and which software and operating systems are being used.
All this data is applied to planning a custom attack depending on the software vulnerabilities they discover.
That is why updates should be installed as soon as possible. For instance, cyber thieves might detect that Windows 7 is being used on an old laptop.
Since Windows no longer supports this operating system, there haven’t been any new updates for years now. Phishers can use this to harm, break into a device, and infect the system with malware.
Prevent hijacking of your smart home
Smart homes have been all the rage lately because they are incredibly convenient and easy to use. Anything and everything can be controlled by a smartphone, even during your absence from the house.
Unfortunately, the Internet of Things, or IoT, could be vulnerable to cyberattacks. There have been numerous reports about hacked smart homes, and the attack can be done with only an internet address.
Internet Protocol information hides plenty of reports, including the model of an Wi-Fi router.
These devices can be easily breached, especially when the default login information remains unchanged for a long time, forget to regularly update firmware, or fail to protect your connection with an app such as a VPN.
Sometimes, there will be no knowledge of a hacked router, but notice the connection is significantly slower and the electricity bill needs to be higher. This is because cybercriminals might use the gadgets connected to the IoT to mine cryptocurrency.
Safeguard your login information
Accessing a network by exploiting an Internet address can lead to even more trouble. For instance, cyber thieves could intercept the files being sent or received, including your login information.
When they learn your email password, phishers will be able to log into social media accounts or even access online banking accounts.
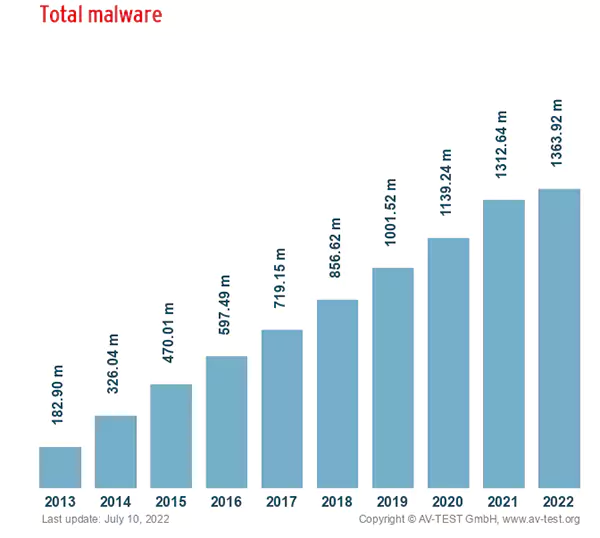
The graph below indicates the urgency to spread awareness about securing IP addresses as the number of malware found over the years has been increasing.
Fend off online tracking
Concealing the Internet Protocol can do a lot for hiding browsing habits that could be used for targeted ads. Websites track online activities and put together a profile with all the preferences and searches.
They might even log on a web address and send targeted ads for specific places. Hiding Internet Protocol can prevent all this and provide a more enjoyable web browsing experience without targeted ads on every website you click on.
How to protect your IP address
We’ve discussed why protecting your web address is necessary, and now is the time to go over the how. Here’s where to start:
- Update your software regularly. Software updates and releases include patches designed to keep all devices safe. So, make sure to run the latest software versions of security tools and operating systems.
- Improve the security of your Wi-Fi network. A home Wi-Fi network as well as a router should be protected by a custom password that is hard to guess. Use encryption, if possible, to ensure no one can eavesdrop on the files being sent and received.
- Use a VPN. A VPN will mask a place and prevent anyone from learning your IP. Users can select a server they want to use, and that Internet Protocol will appear to anyone who tries to uncover someone’s location with the help of an IP tracker. Moreover, a VPN is a well-known encryption tool.
- Ask for a dynamic IP address. This feature might not be available to everyone, but some ISPs offer dynamic web information to their users. When enabling a dynamic IP address, it will occasionally change, which makes tracking and building user profiles a bit harder.
In conclusion, securing an IP address is necessary and does not let phishers infiltrate your device or spread harmful malware. It is imperative that as technology is advancing, more ethical hackers should be trained to take prompt action against cybercriminals. The above suggestions, in this article, will also save your personal data from getting into the wrong hands.
What Is Mobile Proxy And How Do They…
What Is Residential Proxy? Definition And Guide 2024
Protect Yourself from Cybercrime: Top 5 Smart Strategies…
Strategies for Cyber Success: Safeguarding and Managing Your…
Cybersecurity Course Online: Navigating the Digital Threat Terrain
Fortifying Your Online Fortress: Unveiling the Best Paid…
The Imperative of Cybersecurity Integration in Front-End Development…
10 Tricks for Staying Cyber-Secure While Binge-Watching
Securing Your System: The Importance of Anti-Malware Software
Benefits of VPN for Enterprise Networks: Enhanced Security
PureVPN – The Best Streaming VPN
L2TP vs. PPTP: Which VPN Protocol is More…