The Imperative of Cybersecurity Integration in Front-End Development for IT
In the contemporary landscape of relentless digital transformation, the gravity of cybersecurity cannot be overstated.
As data breaches and cyberattacks persistently loom as threats, businesses have unequivocally elevated cybersecurity to the zenith of their IT priorities.
In this comprehensive exposition, we shall delve into the profound implications of cybersecurity integration within the realm of front-end development.
The discerning reader shall come to appreciate the multidimensional nature of this integration and embrace the highest standards of security within this vital IT domain.

The Central Role of Front-End Development
Front-end development, often colloquially referred to as client-side development, constitutes the artistry of sculpting the user interface (UI) and orchestrating the user experience (UX) of digital entities.
It entails the meticulous craftsmanship of digital interfaces, leveraging a medley of programming languages, notably HTML, CSS, and JavaScript. These languages, wielded with precision, breathe life into digital interfaces, rendering them both aesthetically appealing and operationally user-centric.
In light of the pivotal role that it plays in crafting exceptional user experiences, businesses seeking to fortify their digital presence should prioritize hiring an adept professional.
To explore potential candidates, consider visiting https://lemon.io/hire-front-end-developers/, where you can find skilled professionals.
Unveiling the Nexus of Front-End Development and Cybersecurity

Upon initial inspection, development may ostensibly preoccupy itself solely with the superficial veneer of digital products.
However, a deeper examination reveals a symbiotic relationship with the broader cybersecurity landscape. The juncture of these seemingly disparate fields engenders a mutually reinforcing synergy:
- Input Validation: Cyber incursions, more often than not, stem from nefarious inputs. Front-end artisans are tasked with the implementation of exacting input validation mechanisms.
This vigilant scrutiny ensures that user-entered data undergoes rigorous scrutiny, purging it of malevolent intent. The fortification thus thwarts ubiquitous attacks such as SQL injection and cross-site scripting (XSS).
- Authentication and Authorization: The foundational bedrock of the development resides in the meticulous establishment of authentication and authorization frameworks.
Developers must erect secure citadels for user access and privilege management, thereby shielding sensitive user data.
- Secure Communication: Vulnerabilities often lurk in the conduits through which data traverses from client to server.
Its architects play a pivotal role in the implementation of cryptographic protocols, most notably HTTPS and Secure Socket Layers (SSL), ensuring data confidentiality during transit.
- Mitigating Cross-Site Request Forgery (CSRF): Conscientious development serves as a bulwark against CSRF attacks.
The deployment of anti-CSRF tokens and judiciously vetted source validation protocols thwarts malevolent incursions.
- Client-Side Security: The sanctity of the client-side codebase is sacrosanct. Meticulously reducing dependencies on vulnerable libraries and frameworks, and diligently keeping them abreast with the latest security updates, is incumbent upon sentinels.
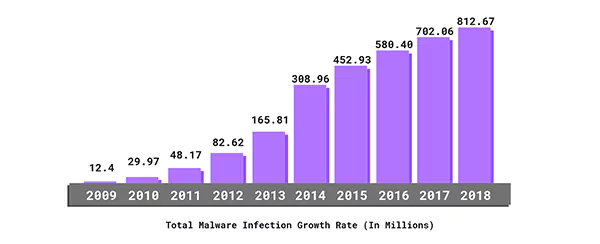
This graph shows the total Malware Infection Growth Rate over the years in millions. With this positive growth slope, you can get an idea of why it is significant to invest in cybersecurity.
As the technology sector started booming after the financial crisis of 2008, there was a sudden rise in malware cases with an exponential growth rate. In 2018, there were more than 812 Million cases recorded. The number is even greater than the whole population of the USA.
Speaking of 2022 statistics of cyber crime alone, stats show that more than 422 million individuals were affected by serious cyber crimes worldwide. According to the FBI’s internet crime records, 800,944 complaints were registered in 2022.
Exemplary Practices for Seamless Cybersecurity Integration in Front-End Development
There are always some cases to treat as a foundation for your course. That said, to attain the zenith of security within front-end development, adhere unwaveringly to these exemplar practices:
- Routine Security Audits: Systematic audits of the codebases, conducted with unrelenting scrutiny, expose vulnerabilities for prompt remediation.
- Meticulous Implementation of Security Headers: Leverage security headers, notably Content Security Policy (CSP) and HTTP Strict Transport Security (HSTS), to erect impregnable defense mechanisms against a gamut of attacks.
- Prudent Library and Framework Adoption: Exercise circumspection when incorporating third-party libraries and frameworks. Vigilance mandates their continuous maintenance and the swift application of security patches to preclude vulnerabilities.
- Adept Error Handling: Institute a rigorous regime of error handling on the client side. It ensures that inadvertent disclosure of sensitive information via error messages remains an implausible outcome.
- Diligent Data Sanitization: The diligent validation and meticulous sanitization of user inputs are cardinal imperatives. Utilizing input validation libraries streamlines this process and ensures data integrity.
- Safeguarding via CORS Configuration: Prudent configuration of Cross-Origin Resource Sharing (CORS) settings averts unauthorized access by meticulously defining the domains permitted to access web resources.
- CDN Security Measures: Adhere to stringent security configurations for your Content Delivery Network (CDN). This safeguards against the injection of malevolent code or inadvertent data exposure.
In Summation
In the current digital milieu, cybersecurity has emerged as an omnipotent sentinel in the realm of IT, and front-end development stands as no exception.
The steadfast integration of robust cybersecurity practices into front-end development is not an optional virtue; it is a solemn obligation. Through this integration, businesses are poised to erect fortifications around user data, safeguard corporate reputation, and defray the catastrophic costs and disrepute associated with data breaches.
It must remain ever-vigilant, stalwarts of security, perpetually attuned to the evolving landscape of cybersecurity threats and best practices.
In an interconnected world where data security reigns as an imperious monarch, cybersecurity integration within the business or IT process is not a discretionary choice; it is a sacred duty. It is the panacea for securing digital assets, preserving user trust, and thriving in an era where cybersecurity is nonpareil.
What Is Mobile Proxy And How Do They…
What Is Residential Proxy? Definition And Guide 2024
Protect Yourself from Cybercrime: Top 5 Smart Strategies…
Strategies for Cyber Success: Safeguarding and Managing Your…
Cybersecurity Course Online: Navigating the Digital Threat Terrain
Are You Being Spied On? 5 Reasons Why…
Fortifying Your Online Fortress: Unveiling the Best Paid…
10 Tricks for Staying Cyber-Secure While Binge-Watching
Securing Your System: The Importance of Anti-Malware Software
Benefits of VPN for Enterprise Networks: Enhanced Security
PureVPN – The Best Streaming VPN
L2TP vs. PPTP: Which VPN Protocol is More…